Over the past few years, both international supervisors, U.S. state regulators, and major rating agencies such as Standard & Poor's and A.M. Best, have adopted regulatory and rating review processes to help ensure that insurers build strong enterprise risk management (ERM) frameworks to help evaluate, govern, and manage risks of loss company-wide.
This year, the National Association of Insurance Commissioners (NAIC) is finalizing a more formalized reporting requirement to monitor risk and solvency levels of the largest insurance companies, going above and beyond the recent state regulatory push towards risk-based financial examinations. The NAIC's Own Risk and Solvency Assessment Proposal (ORSA) is defined as a set of processes used for decision-making and strategic analysis, based on how the company manages and controls its risks.
The goal of performing an ORSA is to analyze, in a continuous and proactive way, the overall solvency and capital requirements of an insurance company in light of the specific business, operational, and underwriting risks uniquely faced by that company. However, an ORSA exercise is not just about capital. It marks a change in behavior, signaling a fundamental shift towards a comprehensive enterprise risk management (ERM) culture. Ultimately, regulators are moving towards supervisory rules and standards requiring insurance companies to integrate risk and risk management in all aspects of corporate day-to-day decision-making.
Under the ORSA requirement, insurers writing more than $500 million of annual direct written and assumed premium, or groups collectively writing more than $1 billion, will be expected to "self-evaluate," using their own internal models, the sufficiency of their capital given a wide range of risks inherent in current and future business operations. As currently proposed, insurers will be expected to detail the elements of their ERM framework and ORSA results in an annual Summary Report to their home-state regulator. Major changes to the ORSA review will be submitted to the regulator on a rolling basis as needed, such as following an update to the company's strategic business plan. In this Summary Report, subject insurers are asked to provide detail in three key sections:
- Section 1 — A description of the Insurer's Risk Management Framework
- Section 2 — An Insurer's Assessment of Risk Exposures
- Section 3 — Group Risk Capital and Prospective Solvency Assessment
To be ready for ORSA reporting by 2014, insurers may be at very different stages of preparedness, depending on how they have allocated resources and budgets to their overall ERM efforts over the past few years. Many companies are running into practical challenges in identifying, organizing, assessing, and managing their necessary risk and control data, which need to be addressed before any reports are compiled. How can companies meet some of those challenges?
Practical Compliance Challenges
Companies may find it challenging to comply with the ORSA requirements for several practical reasons. First, the guidance itself is not strictly prescriptive, giving companies great flexibility in how and what to report in the narrative sections on risk management and control framework or governance process. This means that some companies may provide too much information and some, not enough, and many companies have concerns about privilege, confidentiality and trade secret protection in disclosing information in the amount of detail that regulators might expect.
Second, the basic requirement of Section 1, a description of the insurer's risk management framework, assumes that companies of the stated size already have an overall ERM framework in place, as described. However, even some larger companies may be still working on developing a framework, or may have only a basic ERM program or governance system that they will want to improve on over time, addressing more complex functions or elements.
Third, where companies do have a framework, the framework will not be the same from company to company. There is not yet an established body of "best practices" or standardization of documents, forms, reports, etc. that can simply be adopted or configured for individual entities. Companies continue to look for guidance and recommendations on how to develop solid procedures and practices that will not only meet regulatory minimums for reporting, but can help actually manage, mitigate, and control risk effectively.
With respect to Section 2, the Guidance Manual addresses the insurer's assessment of risk exposures. However, per the NAIC, "one of the most difficult exercises in modeling insurer/group results is determining the relationships, if any, between risk categories." Even where companies are implementing frameworks to create risk and control libraries and score/prioritize risks, it is difficult for insurers to take the "next step" to connecting risks which might have related or "knock-on impact" between departmental functions or areas.
For example, a hurricane may cause (a) underwriting loss (for issued property policies), (b) operational loss (if the company has physical operations or staff in the impacted territory), (c) increased legal, compliance and regulatory costs to comply with state reporting and data call obligations, and (c) cash flow problems, interest loss, reinsurance collection issues, and other financial difficulties due to a sudden run of claims. Some frameworks can accommodate risk measurement but fail to adequately show linkage of interconnected risks.
Further, today management of ERM-related tasks may often be handled informally or haphazardly, without consistent controls in place to confirm that needed action steps, such as risk assessments, have been accomplished. Tracking of activities may be a difficult, manual process, reliant on email spreadsheets and ad-hoc databases without adequate version or content control. With the implementation of the ORSA requirement, insurers may find that they need to "beef up" and significantly improve their documentation, attestation and record-keeping practices generally, particularly of any processes that underlie the ORSA report or feed other ERM-related strategic risk analysis.
Finally, whether preparing for the ORSA, or just implementing ERM for other reasons, insurers may struggle with the balance and tension between their "high level" ERM governance practices, and their day-to-day compliance or operational management functions. Companies constantly struggle to improve a wide variety of internal controls, policies and procedures. However, with the implementation of ERM protocols which rate/rank control effectiveness, and attest to the operation of risk mitigation procedures, gaps and deficiencies in controls may become more obvious, and reveal the need for more resources in functional areas. Prioritizing and scoring risks and controls within an ERM program may, over time, actually lead to a shift of internal resources and management focus away from original goals of analyzing high-priority risks. Additionally, it may result in using ERM information for strategic planning, back to the nitty-gritty detail of better inventorying or managing operational, compliance, legal and regulatory risks.
Recommendations
More than ever before, the ORSA reporting requirement will require insurance companies to assimilate strong risk and control management practices into all aspects of everyday corporate decision making, from setting financial strategies and establishing business plans, to controlling routine compliance, legal, and operational risk. Companies must widen and solidify the links and inter-relationships between all departments and functions that might impact either corporate losses, or business opportunities. What can be done?
Don't wait to design a solid ERM program until regulatory reporting demands are imminent; develop a more integrated program of risk and control assessment and management now.
Even in companies which historically have a strong focus on compliance or internal control issues in specific functional areas such as finance, claims or underwriting, the process of implementing an integrated program of risk identification, assessment and control on a larger scale - across an organization - can take many months, if not years. It takes time to review and catalog what controls are currently working, or not, and put remediation plans in place. It takes time to roll out new risk assessment and communication protocols to key staff. It also takes time to determine what risks are higher in potential impact to the company, and thus, where to dedicate resources. Waiting until the last minute to start even a rudimentary review process, with the thought "we'll do it when we know exactly what regulators want us to report," will be too late to embed and test the success of expanded risk management tools and techniques.
Build on the company's current risk and control management expertise, and keep control-related functions well-coordinated.
To ensure thorough review of risks and controls, as well as to prevent duplicating work, look for potential synergies between the ERM process and other control functions, such as legal and regulatory compliance, internal audit, and operational management teams. Try to integrate ERM/ORSA record keeping and supporting tasks with other uses for related data, such as SOX certifications, regulatory compliance or market conduct compliance management audits, and any other processes that involve any review or analysis of potential loss to the company.
For example, any process asking employees to sign off on or attest to the effectiveness of policies and procedures, SOX "key controls," or other controls mitigating risks should be discussed with team members from other compliance-type functions to see if the sign-off process can be timed, or documents drafted, to be used for multiple purposes. Also, members of the various departments responsible for the tracking of emerging risks, financial models, or the development of business plans should liaise on a regular basis, to help ensure a consistent approach to those important planning processes.
Invest in technology to ensure risk information will be assessed and prioritized effectively, to help create links between risks in different areas, and to streamline workflows.
Understanding and managing the quality and availability of existing information within the insurer is key to a successful ERM or ORSA implementation. Whether adopting ERM to comply with regulatory challenges, to meet rating agency expectations, or just as a good business practice, companies should not limit their technology and planning efforts to the actuarial modeling of risk, or calculation of capital. Rather, implementing ERM should be viewed as a key opportunity to improve existing control processes and reporting tools, and to automate as many processes as possible.
In sum, the NAIC's ORSA approach continues to evolve rapidly. Investing time and resources now to improve overall compliance and control efforts, and establish solid enterprise-wide risk assessment, documentation, and communication, should go a long way to meet upcoming ORSA reporting obligations. Ultimately, having a complete, solid ERM framework, integrated with other company compliance and control functions, should be a strong foundation for insurers' long-term risk-based capital assessment goals.
20 Sep, 2012
-
Source: http://www.propertycasualty360.com/2012/09/20/meeting-todays-compliance-challenge-erm-orsa?ref=rss
--
Manage subscription | Powered by rssforward.com











 Competition among bed & breakfasts, a thriving sector in the hospitality industry, has led many B&Bs to expand their offerings to include activities that promise a more adventure-based stay—creating exposures that provide agents and brokers inroads to new or expanded business.
Competition among bed & breakfasts, a thriving sector in the hospitality industry, has led many B&Bs to expand their offerings to include activities that promise a more adventure-based stay—creating exposures that provide agents and brokers inroads to new or expanded business. The clientele interested in such adventures are mainly Baby Boomers—older couples with empty nests, looking for comfort and adventure close to home, says Brent Skiles, assistant vice president of underwriting for Philadelphia Insurance Cos. in Bala Cynwyd, Pa. And so far, he adds, these expanded offerings have been good news for the B&B insurance market.
The clientele interested in such adventures are mainly Baby Boomers—older couples with empty nests, looking for comfort and adventure close to home, says Brent Skiles, assistant vice president of underwriting for Philadelphia Insurance Cos. in Bala Cynwyd, Pa. And so far, he adds, these expanded offerings have been good news for the B&B insurance market.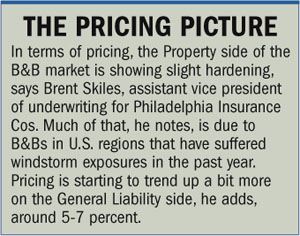 When it comes to some of the new exposures, Philadelphia Insurance Cos. has a Guides and Outfitters program through its Gillingham & Associates insurance arm to cover activities like hunting, boating, fishing, hiking, biking, photography tours and horseback riding. Outdoor Insurance Group of Louisville, Colo. offers stable and trail-ride insurance, coverage for ATV and snowmobile tours, and a B&B package that includes Equine Liability.
When it comes to some of the new exposures, Philadelphia Insurance Cos. has a Guides and Outfitters program through its Gillingham & Associates insurance arm to cover activities like hunting, boating, fishing, hiking, biking, photography tours and horseback riding. Outdoor Insurance Group of Louisville, Colo. offers stable and trail-ride insurance, coverage for ATV and snowmobile tours, and a B&B package that includes Equine Liability. All B&Bs have to have General Liability and Property insurance, and if they have a liquor license, a Liquor Liability policy is also required, Montgomery says.
All B&Bs have to have General Liability and Property insurance, and if they have a liquor license, a Liquor Liability policy is also required, Montgomery says.